NordVPN Threat Protection
Our Review
Quick Summary
At Akali SEO, we understand the importance of online security. That's why we're excited to introduce you to NordVPN Threat Protection, your shield against digital threats in the vast cyber landscape.
Over the past few years, there has been a noticeable increase in cases where people's credit card details and bank login information have been exposed to unauthorised individuals, especially overseas.
In this review we will explore how NordVPN takes a unique and innovative approach which allows you to act before a scammer can charge your credit card or perform various illegal activities under your name.
NordVPN is compatible with a wide range of devices, including Windows, MacOS, Linux, Android, iOS, Chrome, Firefox, Edge, and Android TV, ensuring seamless protection across platforms, including popular mobile devices such as Samsung and iPhones.
The official website of the Queensland Government Australia and ACSC recommend the use of Virtual Private Networks (VPNs) as a means of enhancing data protection.
It offers the convenience of simultaneous compatibility with up to 6 devices, allowing you to secure multiple devices under a single subscription of $3.19 per month. You can install NordVPN software on as many devices as you like, the six device limit only applies to how many simultaneous VPN connections you can use at one given time. You can even connect NordVPN directly into your Wi-Fi router and it only counts as 1 out of the 6 devices.
Our dedicated team at Akali SEO has conducted rigorous testing of NordVPN and its comprehensive suite of features. After thorough evaluation, we highly recommend NordVPN for both personal and business use.
| Personal-Use | Business-Use | |
|---|---|---|
| Threat Protection | ||
| Meshnet | In some cases | |
| VPN | ||
| Dark Web Monitor |
We invite you to take the next step by reading our full NordVPN review below or to visit NordVPNs official website and experience an unmatched level of online security and privacy it provides.
Lets take a deep dive and test each component in our comprehensive NordVPN 2023 review below.
Threat Protection
NordVPNs inbuilt anti-virus
We initially began our search for software primarily for this reason, anti-virus threat protection.
Over the years we have seen many types of deceptive cyber-attacks, the most common is the typical email invoice which looks legitimate.
Once a virus is opened it can infect important files on your PC rendering them inaccessible, including commonly used ones such as:
- PDF files
- Word documents
- Excel files
- Sentimental photos of family & friends
There are two approaches when it comes to dealing with Malware & Viruses.
- Reactive - Dealing with the Malware after it is opened
- Proactive - Preventing the Malware from opening in the first place
Reactive IT support often can't recover important files unless you had a good backup system. They usually remove the infection, leaving you with an empty PC and lost files.
Taking a proactive approach is far better and will prevent the virus at it's direct source.
NordVPN prioritises proactive protection over reactive recovery with its inbuilt Threat Protection feature.
Prevention is key. Say goodbye to phishing scams that attempt to trick you with deceptive emails.
But what would our words be if we didn't actually test it? Let our team at Akali SEO open a virus to test.
This test is provided by highly trained IT professionals for educational purposes only, please do not replicate it in any way or form.
Eicar is our test virus file which downloads seamlessly with no detection.
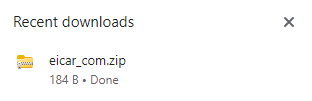
Now lets open our NordVPN Panel and turn protection ON.
The Eicar virus no longer downloads onto the desktop.
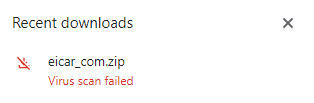
NordVPN lets us know that the file was removed.
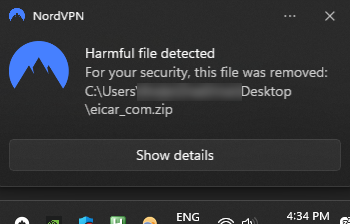
We can see within our NordVPN logs of Malware detected and automatically deleted.
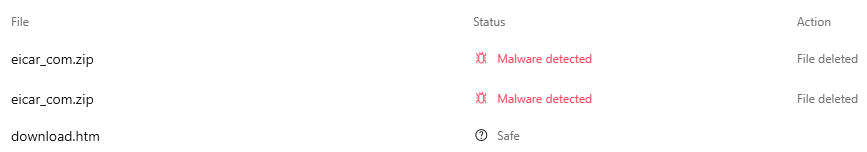
In this instance, it is evident that NordVPN has effectively stopped the Malware. The implementation of proactive measures, such as NordVPN's Threat Protection feature, can yield substantial cost savings for businesses, potentially amounting to thousands of dollars in avoided recovery expenses.
Also as demonstrated, it effectively safeguards individuals from potential breaches, preventing unauthorised access to sensitive bank login and credit card details within the confines of those using it at home for personal use.
Meshnet
Create a secure network for easy file transfer between devices
We love this feature as it instantly makes a business more productive by speeding up staff collaboration, and in fact, we use it at Akali SEO.
Networks can get confusing, to put it simply, we are going to jump straight into an example of:
How a Medical Clinic can apply Meshnet to their business to share one folder for all employees to access.
The Medical Clinic has a folder on their desktop called Meshnet which they require all staff members to be able to put patient files in for other doctors and admin staff to access, immediately & securely at any time.
With Meshnet switched on and the proper folder sharing permissions set, your device name can be copied.
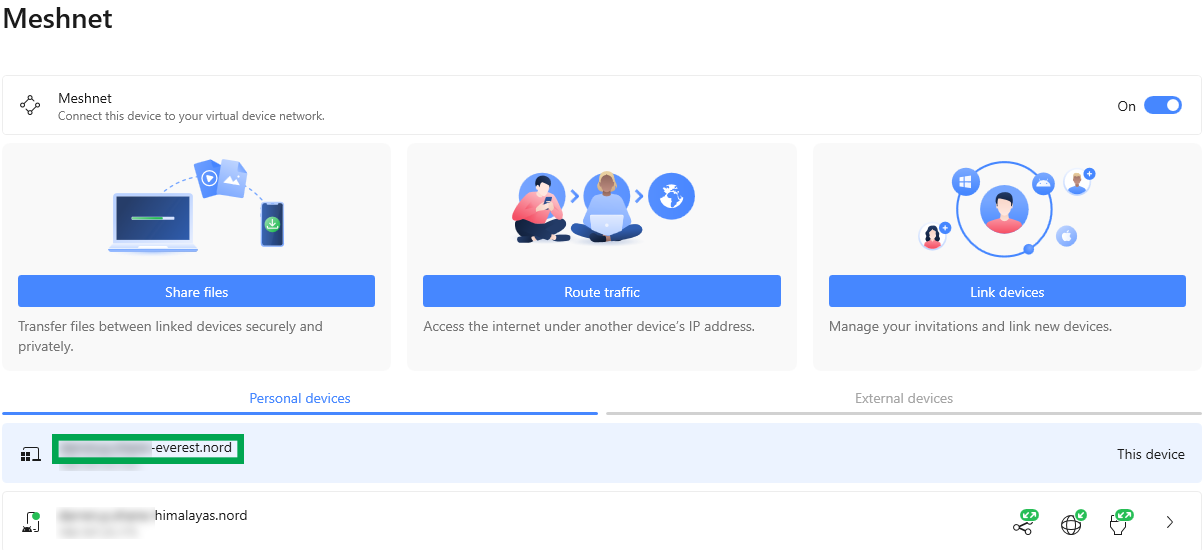
Any staff member can enter the device name in file explorer to access the exact same Meshnet folder in real time, on any device with Meshnet switched on.
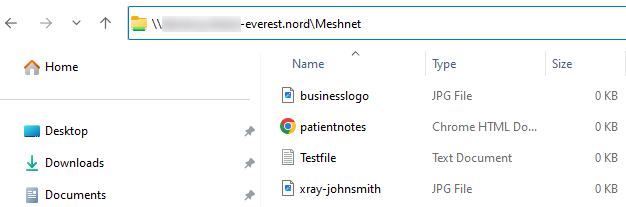
We have placed a shortcut on every staff members computer for easy access to drag and drop files into it.
Now all employees with Meshnet can have the same folder updated instantly as they drop files into it, no matter where they are in the world. Remote workers can now collaborate in other countries by dragging and dropping files securely with Meshnets NordLynx protocol technology which is safe when using Airport Wi-Fi for secure file transmission.
As a bonus, we enjoy using Meshnet at home to quickly send photos from our mobile devices to the PC to free up mobile storage.
VPN
Protect yourself from public Wi-Fi monitoring
Depending on which router you are connected to, you may be connected to a Wi-Fi that can spy on your browsing.
Primarily mobile devices & portable laptops using Wi-Fi are vulnerable to spying as you are travelling and connecting to other peoples Wi-Fi.
VPNs put simply, is a secret tunnel for your internet connection to protect it from prying eyes. We recommend it, and this recommendation is also mentioned by the Queensland Government website and ASCS (Australian Cyber Security Centre).
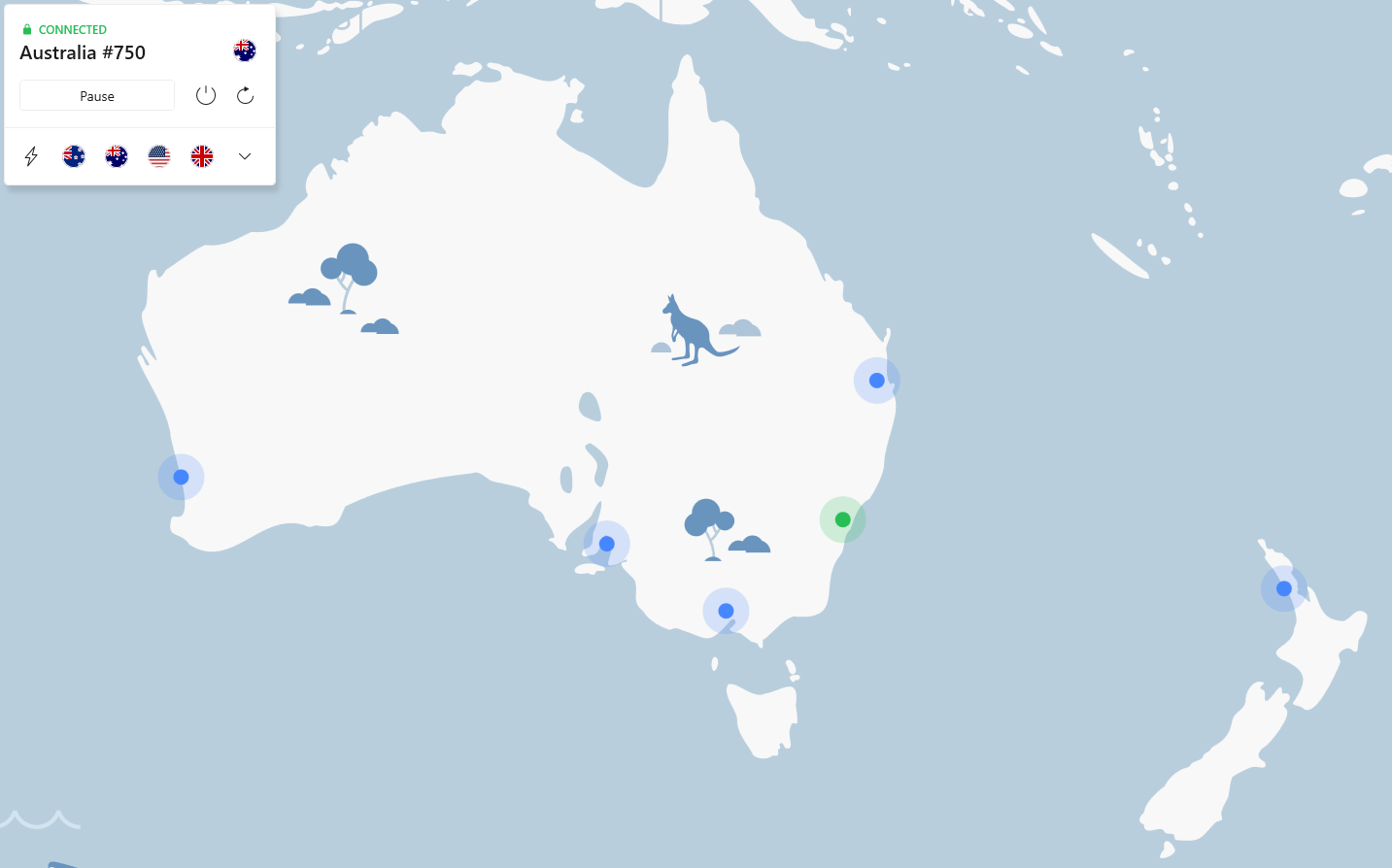
In the NordVPN Australia interface depicted below, seamless connections within Australia and to various international locations are effortlessly achievable. Moreover, you have the option to automate connections upon booting up your computer or mobile device.
Once connected, your IP address is masked and protected for safe browsing. It is recommended you connect to your nearest location for the fastest speeds.
Preventing DOS (Denial of Service) Attack
Another reason to hide your IP address is to protect yourself from more sophisticated attacks such as a DOS (Denial of Service) Attack.
Below is our testing on how easy your internet can be disabled, from a simple email reply to a malicious actor.
This test is provided by highly trained IT professionals for educational purposes only, please do not replicate it in any way or form.
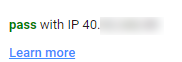
From an existing email, we find the IP address of the sender.
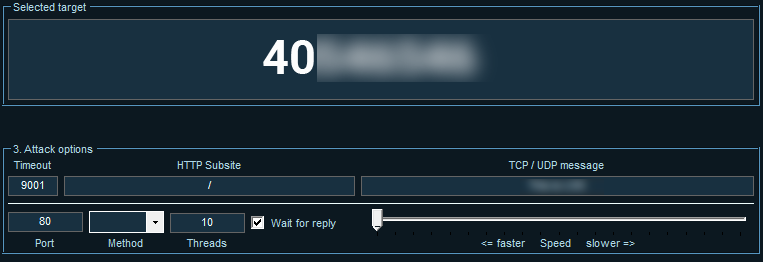
We conducted an internal test using a network stress testing tool which sends many packets and overfloods the destination IP address, essentially bringing the internet access to a halt.
If we had NordVPNs switched on, our personal IP address would be hidden which renders the spying & attacks useless.
Connect to public Wi-Fi or airport networks with confidence, knowing that NordVPN is safeguarding your IP address.
Dark Web Monitor
Take action on identity theft and credit card fraud before it occurs
The dark web is a hidden part of the internet where websites and activities are often anonymous, making it a place where both legal and illegal things can happen without easy tracking.
NordVPNs Dark Web Monitor constantly checks your email address to see if your data has been leaked and notifies you accordingly to take action.
Some common examples of leaked information include:
- Email Address
- Home Address
- City
- Country
- Date of Birth
- Full Name
- Phone
- State
- Postcode
- Passwords
With this above information, it is very easy for someone to impersonate you and take a loan under your name or simply login with a breached password to make purchases in your online shopping accounts.
NordVPN's Dark Web Monitor keeps a watchful eye on the web's shadowy corners, ensuring that your personal information hasn't fallen into the wrong hands.
It detects which logins have been breached and lists it in detail so you can take control of your digital identity and contact the respected parties that were breached.
Conclusion
NordVPN has passed our tests, it emerges as a formidable ally in safeguarding your online presence. Our extensive testing affirms its prowess in shielding your data from cyber threats, bolstered by robust encryption and innovative features such as Threat Protection and Dark Web Monitoring. We have monitored NordVPN over the years and believe the innovation is going to continue as they release new features over time.
NordVPN is easy to install and use for beginners, its impressive VPN internet speed performance and Threat Prevention make it an ideal choice for business and personal at home use.
Frequently Asked Questions
It also monitors the dark web for any leakage of your personal information, enabling you to promptly contact sensitive organisations like your bank to secure your accounts and cards before any scam can take place.
Meshnet is designed to be non-cloud and P2P-based, which means it inherently cannot collect data as part of its function.
Disclosure: Links on this website are affiliate links of which we may receive a small commission, but the price either remains the same (or in most cases is discounted for you). We only affiliate with products that we have fully tested and can see it providing value to our clients.

